Information security risk management framework
In order to strengthen the security and management of information operations, the company has established an inter-departmental information security committee to formulate information security management policies, promote "information processing regulations", coordinate inter-departmental information processing operations, review the company's information security policy and implementation results, and promptly report to the board of directors on the company's information security management. The information security committee is framed as the following chart:

Information security policy objectives
Ensure the confidentiality, integrity and accessibility of information assets, and protect user's information privacy.
Ensure the normal operation of all the company's information operating systems, maintain the security of network information, and ensure the confidentiality and integrity of the company's computerized data. Information management, system development and program modification, preparation of system documents, programs and data access, data input and output, data processing, computer file and equipment security management, hardware and system software purchase, use and maintenance, system recovery plan formulation and testing procedures, information communication security management, system or mail account password applications, etc. are all within the scope of information security management.
|
Information Security Committee
Internal and External Audit
Each Department
|
 |
Information security management measures
| Categories | Description | Related Procedures |
|---|---|---|
|
Authorization Management |
Management of each system account and authorization |
|
|
Accessibility Management |
Access management Access to internal and external data, letter transmission, control through filtering |
|
|
External Prevention |
Network security, anti-virus software, outsourcing and third-party supplier |
|
|
System Repair |
System usage status, handling measures for disconnection |
|
|
Database management |
Database backup |
|
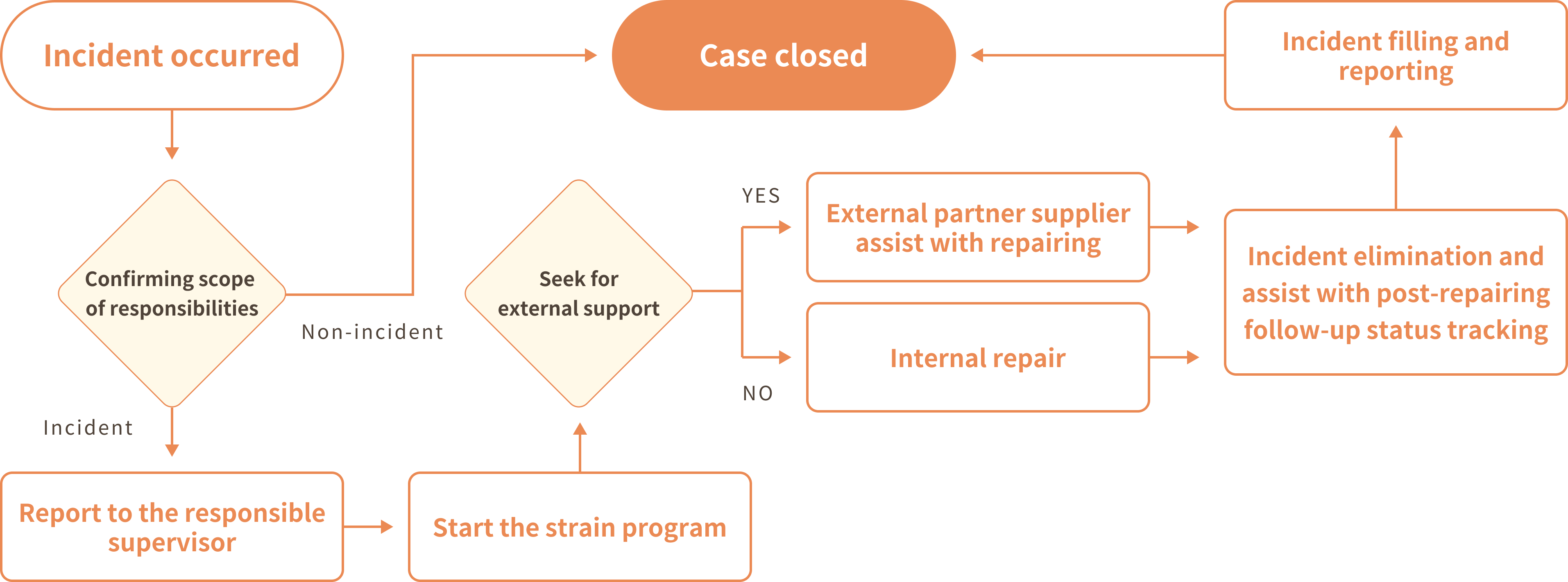
The emergency strain plan of the company's information system is as follows. The reporting and handling of information security incidents should all be performed in compliance with the procedures.